Planning ahead is required before choosing a VPN solution to make sure that the VPN solution addresses your needs.
We will next discuss about the available VPN solutions on the market these days:
PPTP VPN
Let's begin with PPTP. This is also called as the point-to-point tunneling protocol.
Now although this was a widely-used VPN solution on the old windows machines, it is not considered secure anymore.
There are some known problems with PPTP protocol. Let's see what these are:
PPTP uses TCP port 1723 and IP protocol 47. This is important when it comes to permit PPTP traffic to pass through a firewall if you're configuring such a vpn.
- Point-to-point tunneling protocol uses the generic routing encapsulation, otherwise called GRE, for tunnel establishment. GRE stands for generic routing encapsulation and it is the basic of a vpn tunnel.
- This is used, in other words, to create a point-to-point VPN connection.
L2TP VPN
- L2TP vpn is built on the IPsec protocol.
- L2TP stands for layer 2 tunneling protocol, where layer 2 stands for layer 2 of the OSI model, the data link layer.
- L2TP with IPsec uses a number of ports that need to be opened in the firewall, such as TCP1701, UDP 500 and UDP4500, and it uses IP protocols 50, for Encapsulating Security Payload, or ESP, and IP protocol type 51 for Authentication Header, or AH.
- With L2TP and IPsec, we have several authentication options:
- either configure a pre-shared symmetric key that is configured the same on both ends of the connection which is then used to establish communication,
- or we can use a PKI certificate, which is considered a much more secure solution than a pre-shared key.
- And depending on the specific vendor implementation, such as Microsoft's implementation of working with IPsec, we could also use other types of authentication methods:
- like Kerberos which is used by Active Directory.
- SSL - stands for secure sockets layer
- TLS - stands for transport layer security.
With the latest in security threats, VPNs are becoming more and more popular.
You'll often see SSL and TLS used together, however, we need to know that SSL has some security flaws, whereas TLS is considered to be secure (until now).
This type of VPN uses TCP port 443. Now this is considered firewall friendly, because at least in an outbound direction from within a network, normally TCP 443 traffic is allowed out because it's used for secure web browser communications, in other words, HTTPS.
In order to use an SSL or TLS VPN, PKI certificates are required where public and private keys are required.
Remote access or client to site vpn
This is often used for a client-to-site VPN (remote access or gateway vpn), so you won't see SSL or TLS VPNs used in site-to-site VPNs.
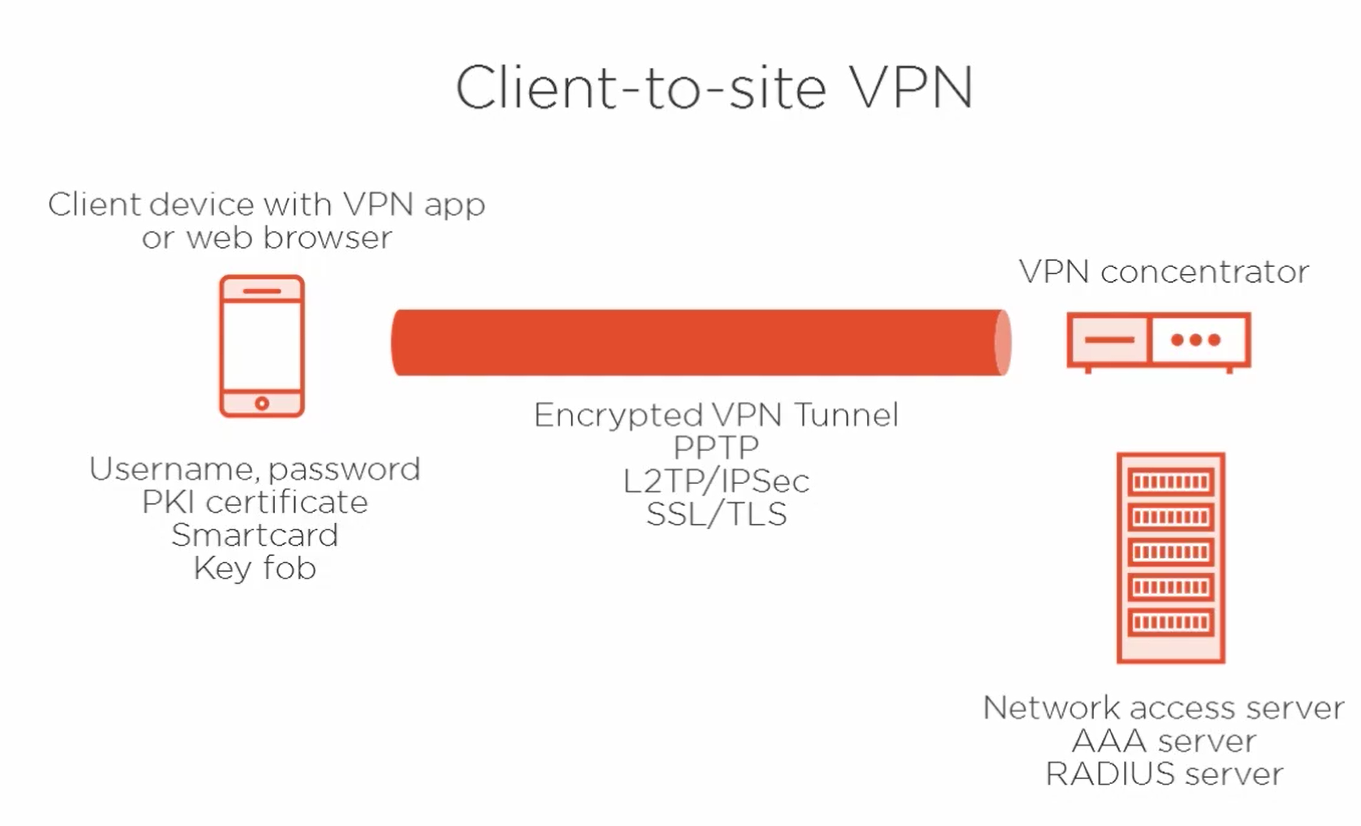
On the screen, we have a basic diagram of a client-to-site VPN, where over on the left we've got the client device with either a VPN client application installed or using a web browser such as for an SSL VPN.
Now the user on the client device can authenticate in a number of different ways:
- using username and password
- or a PKI certificate
- or a smart card
- or a key fob
- or a combination therefore.
Now over on the right we've got the VPN appliance that is capable to receive multiple client VPN connections simultaneously.
And after that tunnel has been established, that can be done using PPTP, L2TP/IPsec, or SSL or TLS, but after that's established, it's only because successful authentication will have occurred to establish the encrypted tunnel.
And pictured at the bottom right of our diagram, that can be done, ideally, using a network access server.
We usually do not want credentials checked for users directly on the VPN concentrator itself for security reasons, because it is considered an edge point device.
Now the network access server can also be called an AAA server or a RADIUS server. They all really mean the same thing. It's another centralized authentication host outside of the VPN device.
Site-to-site VPN
these are used to link offices together, for example, over the internet or over a dedicated leased line.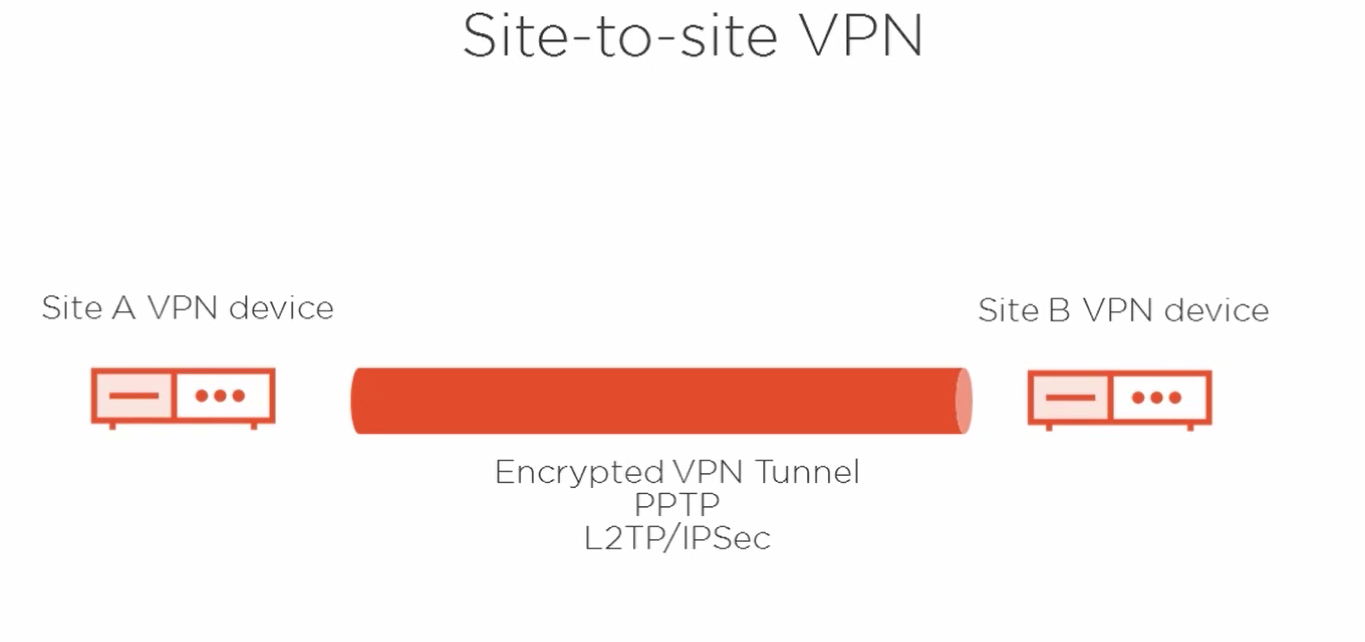
So on the left we've got our Site A VPN device, on the right our Site B VPN device.
Notice we don't have VPN clients involved, at least not directly at this point. So our encrypted VPN tunnel, then, could use PPTP or Layer 2 Tunneling Protocol in use with IPsec. So the clients at each site would then be able to connect to the other site by going through this VPN tunnel. It's simply a matter of IP routing from the client perspective in a site-to-site VPN scenario.